Password Hacking tools: 10 Techniques to prevent cracking and protect your accounts. In today’s digital age, password security is more critical than ever. Hackers use various techniques to crack passwords and gain unauthorized access to accounts and systems
Table of Contents
Password Hacking tools: Techniques to prevent cracking and protect your accounts
To prevent password cracking attacks, it’s essential to understand these techniques and take appropriate measures to protect your passwords
Password cracking
Password cracking is the process of guessing or cracking a password in order to gain unauthorized access to a system or account. Hackers use various techniques to crack passwords, and it’s essential for individuals and organizations to understand these techniques to prevent password cracking attacks.
Here are the top 10 techniques used by hackers and how to prevent them:
Brute Force Attack:
A brute force attack is a technique used by hackers to guess a password by trying every possible combination of characters until the correct password is found. This technique is time-consuming, but it can be effective for cracking weak passwords.
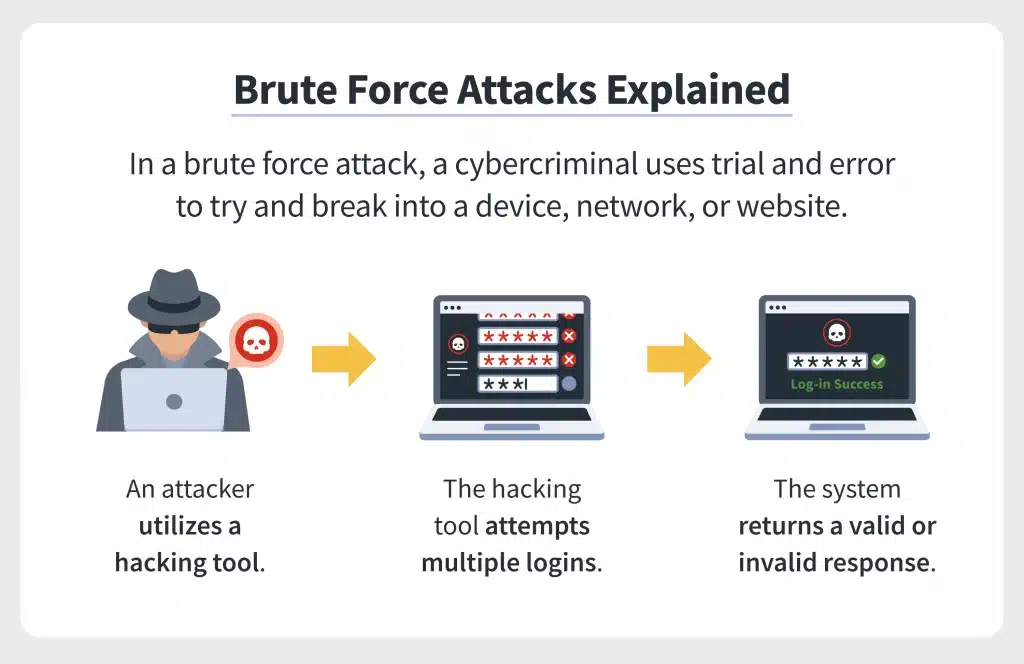
To prevent brute force attacks, use strong passwords that are at least eight characters long, contain a mix of uppercase and lowercase letters, numbers, and symbols, and avoid using common words or phrases.
Dictionary Attack:
A dictionary attack involves using a list of words or phrases to guess a password. This technique is more efficient than brute force attacks because it uses a predefined list of commonly used words, phrases, and commonly used passwords.
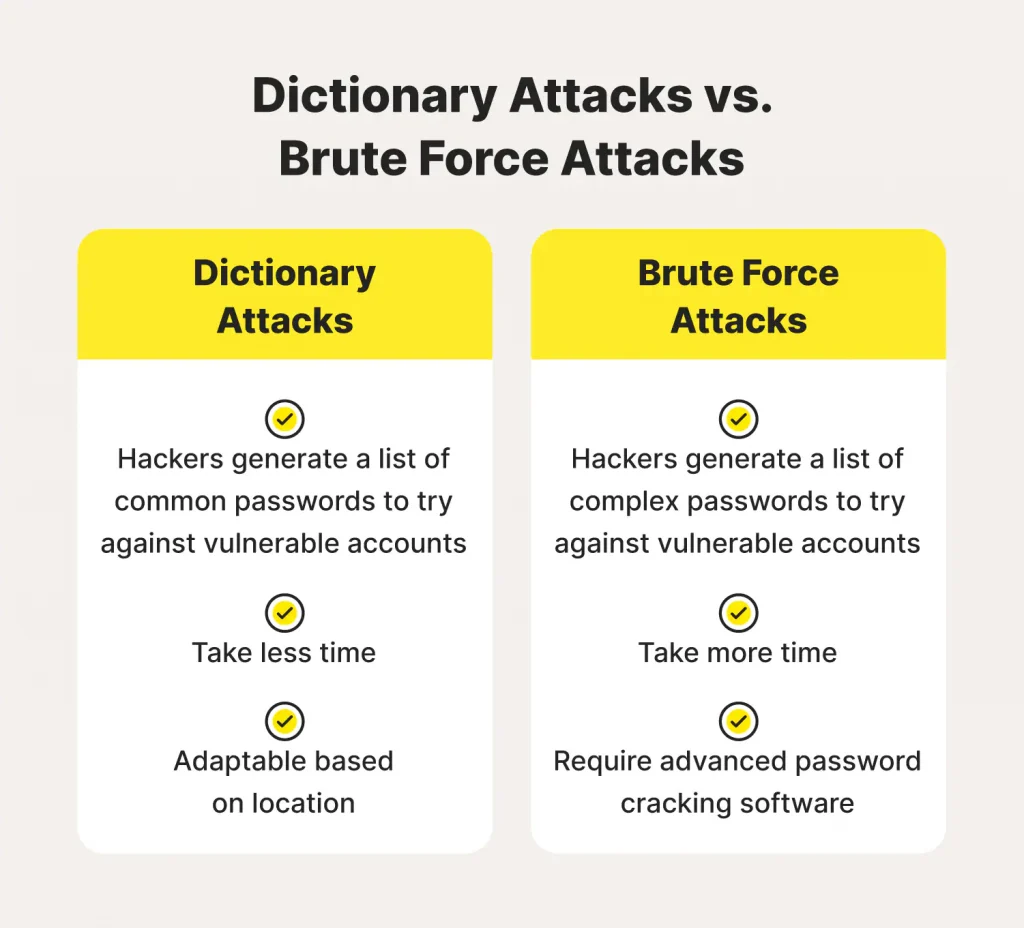
To prevent dictionary attacks, use complex and unique passwords that are not found in dictionaries or wordlists.
Rainbow Tables:
A rainbow table is a precomputed table of hashes for every possible combination of characters. When a hacker gets a hash of a password, they can search the rainbow table for a matching hash and retrieve the password.
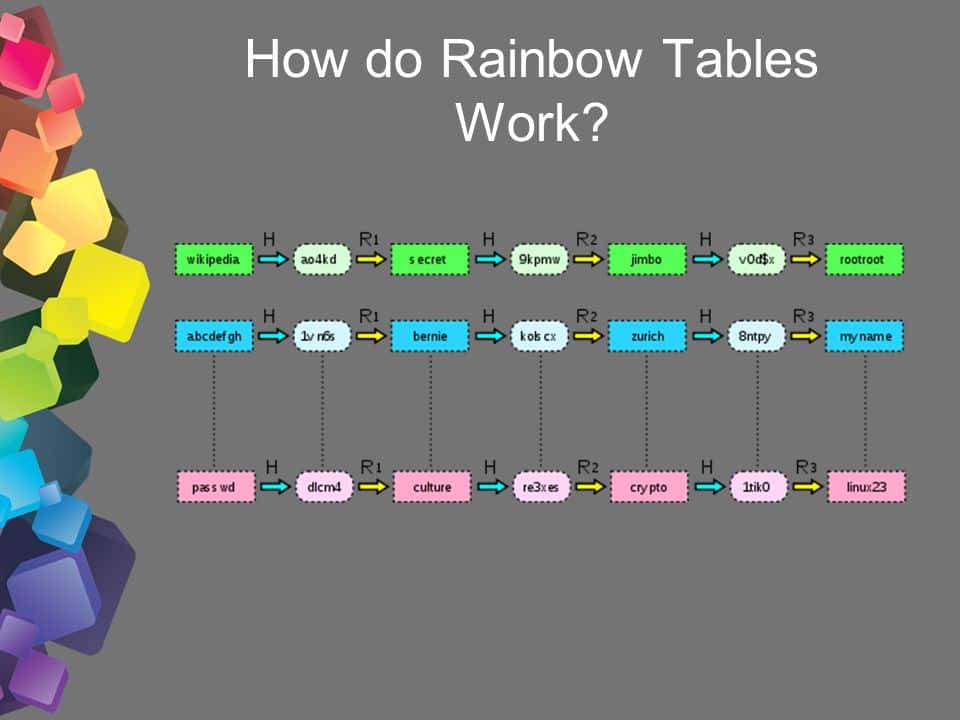
To prevent rainbow table attacks, use salted passwords that add random data to the password before hashing it, making it harder for hackers to use precomputed tables.
Keylogger:
A keylogger is a type of malware that records keystrokes and sends them to the attacker. When a user types their password, the keylogger captures it and sends it to the hacker.
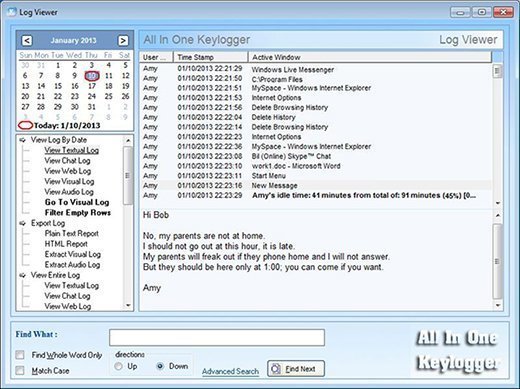
To prevent keylogger attacks, use an up-to-date antivirus software, do not click on suspicious links, and avoid installing software from untrusted sources.
Phishing:
Phishing is a social engineering technique used to trick users into revealing their passwords. Hackers create fake websites or send emails that mimic legitimate ones to get users to enter their login credentials.
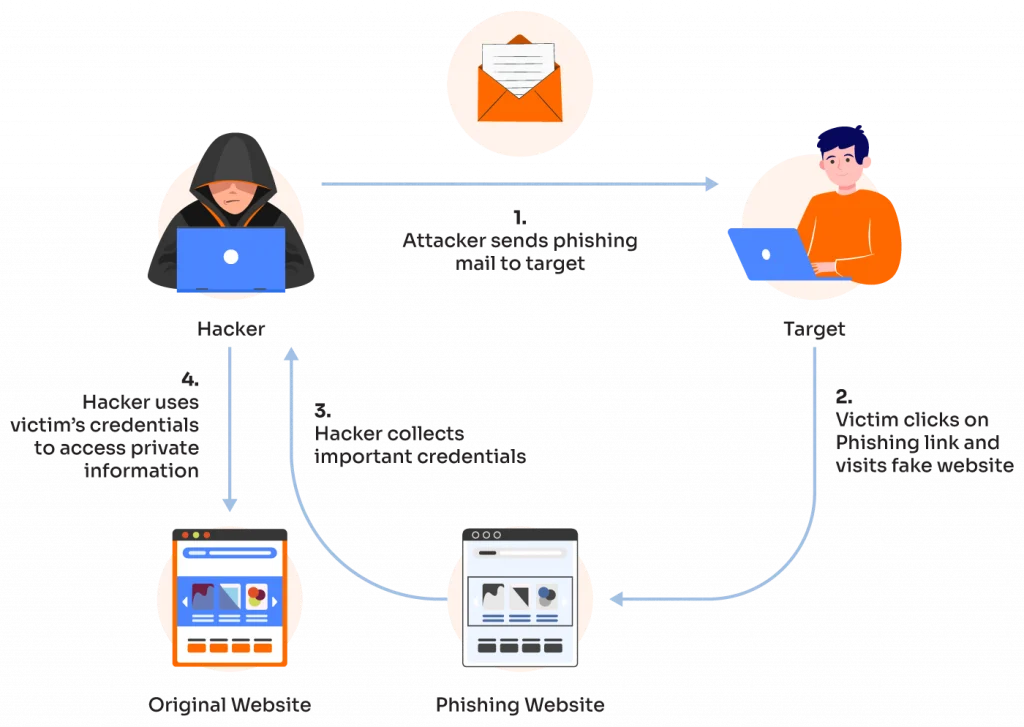
To prevent phishing attacks, be cautious of emails or websites that ask for sensitive information, verify the authenticity of the website or sender, and use two-factor authentication.
Shoulder Surfing:
Shoulder surfing is the act of looking over someone’s shoulder to obtain their password.

To prevent shoulder surfing attacks, be aware of your surroundings and avoid typing passwords in public places where others can easily see them.
Social Engineering:
Social engineering is a technique used to manipulate users into revealing their passwords. This can include posing as an IT support technician or using other persuasive tactics to gain a user’s trust.
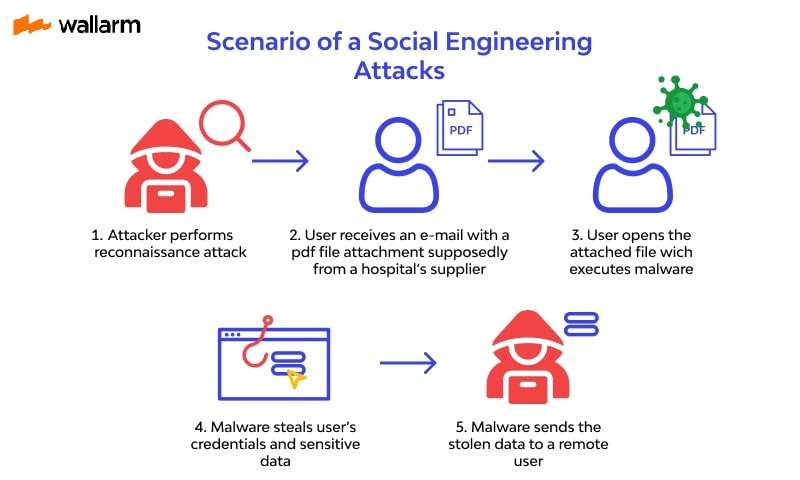
To prevent social engineering attacks, be cautious of unsolicited emails, calls, or texts that ask for sensitive information, and verify the identity of the requester.
Password Reuse:
Password reuse is using the same password across multiple accounts. Hackers can use this to gain access to multiple accounts if they are able to crack one password.
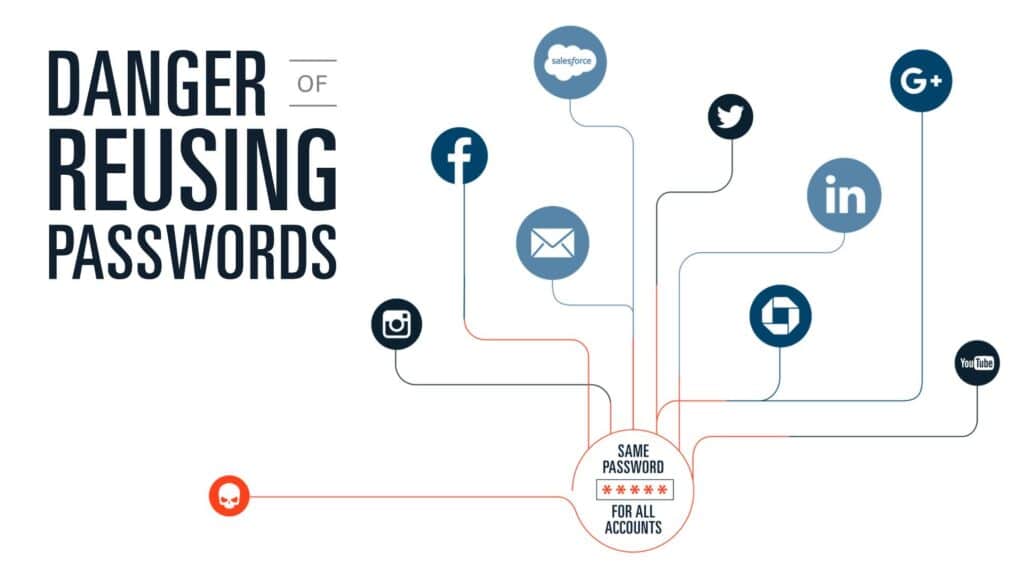
To prevent password reuse attacks, use unique passwords for each account.
Insider Threats:
Insider threats involve trusted individuals with access to sensitive information who may abuse their access or accidentally reveal passwords.

To prevent insider threats, limit access to sensitive information and regularly monitor and audit employee access.
Credential Stuffing:
Credential stuffing involves using stolen credentials from one website to gain access to another website where the user uses the same login credentials.
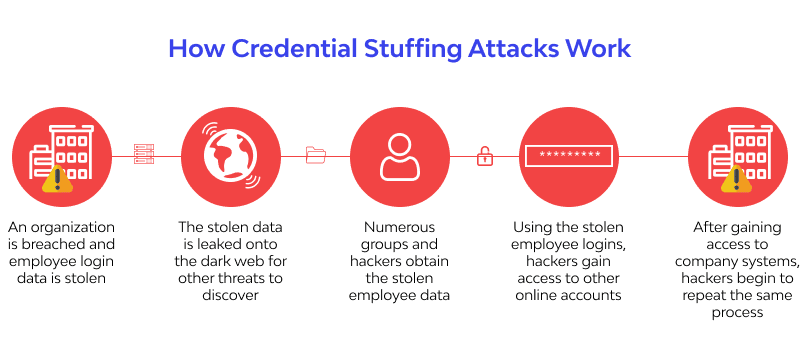
To prevent credential stuffing attacks, use unique passwords for each website, and use two-factor authentication.
Tools to crack passwords.
In addition to these techniques, hackers also use various tools to crack passwords. These tools include:
Hashcat:
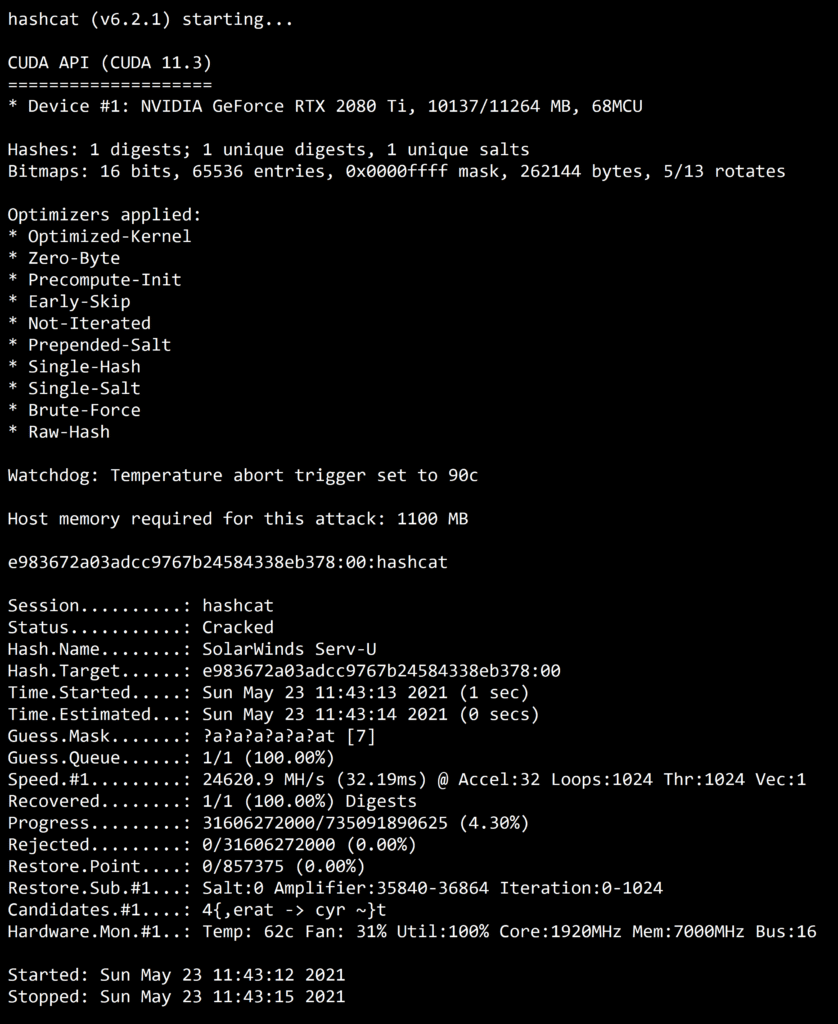
Hashcat is a password cracking tool that uses various techniques to crack passwords, including brute
John the Ripper:

John the Ripper is a free and open-source password cracking tool that can perform various types of attacks, including brute force, dictionary, and hybrid attacks.

It supports various operating systems, including Windows, Linux, and macOS.
Cain and Abel:
Cain and Abel is a password cracking tool that can recover various types of passwords, including network passwords, Windows passwords, and more.
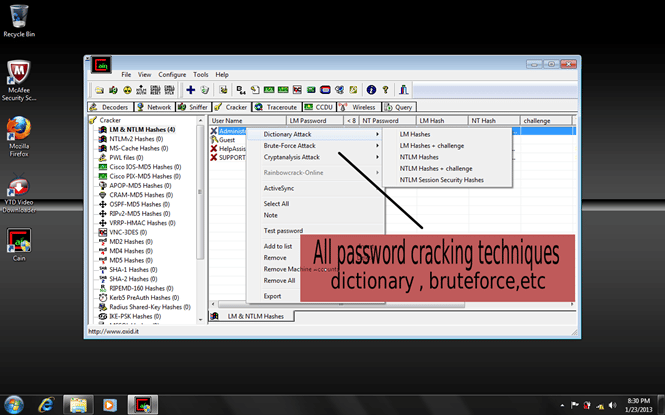
It also includes a sniffer and a password recovery tool for several protocols.
Aircrack-ng:
Aircrack-ng is a password cracking tool used for Wi-Fi networks. It can crack WEP and WPA/WPA2-PSK encryption using dictionary and brute force attacks.
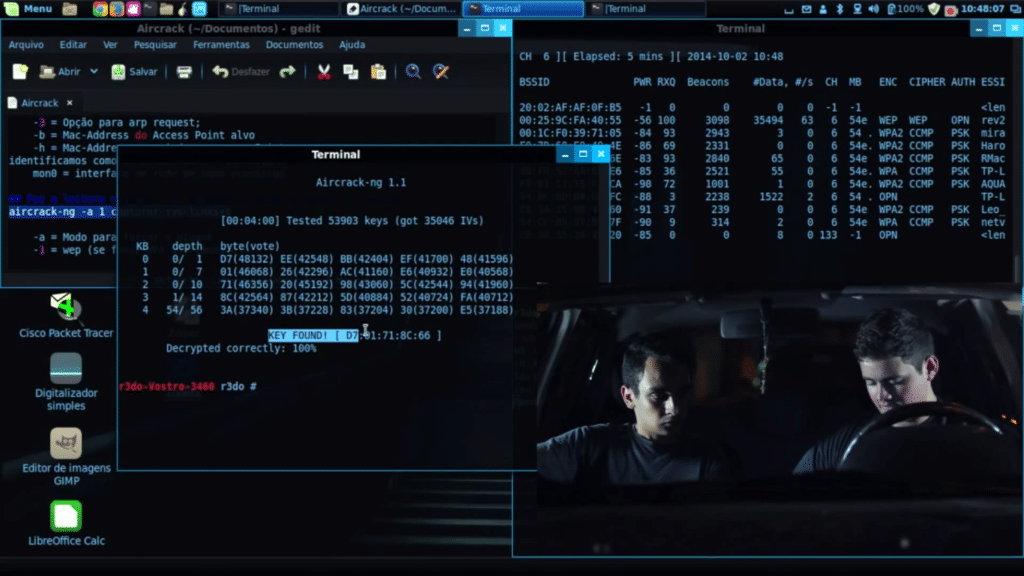
It supports various platforms, including Windows, Linux, and macOS.
Hydra:
Hydra is a network login cracker that can perform brute force, dictionary, and hybrid attacks. It supports various protocols, including FTP, SSH, Telnet, SMTP, and more.
RELATED: Flipper Zero – Hottest Hacking Device for 2023
To prevent password cracking attacks, use strong and unique passwords, avoid password reuse, use two-factor authentication, and keep your software and antivirus up-to-date. It’s also essential to educate yourself and your employees about password security best practices and regularly monitor your accounts for suspicious activity
Here is where we share source of knowledge (Life Hacks & Life Style ), Entertainment, Technology, Fashion, E-News and updates all over the world.
Keep on visit our website for more updates

