Kali Linux Penetration Testing Bible PDF Book download. Kali Linux Penetration Testing Bible is a comprehensive guide to using the Kali Linux operating system to conduct penetration tests and security assessments.
Table of Contents
It starts with an introduction to the fundamentals of penetration testing and security assessment before diving into the specifics of the Kali Linux operating system and its tools.
| Name Of Article | Kali Linux Penetration Testing Bible PDF Book download. |
|---|---|
| Technology | Check Here |
| Life Hacks | Check Here |
| Life style | Click Here |
It covers topics such as network reconnaissance and mapping, vulnerability scanning, exploitation, privilege escalation, password cracking, post-exploitation, and reporting. It includes detailed instructions on how to use the many tools included in Kali Linux, as well as how to customize the system for specific testing scenarios.
Kali Linux Penetration Testing Bible PDF Book download.
The book also contains detailed explanations of the different types of attacks, and provides guidance on how to develop attack strategies and defend against them.

Finally, the book contains practical advice and real-world examples of penetration testing in action.
RELATED: Step by Step Setting up a Virtual Hacking Lab
With this book as a guide, readers can become more skilled at using the Kali Linux operating system to conduct penetration tests and security assessments
Introduction to Penetration Testing and Security Assessment
This chapter provides an introduction to the fundamentals of penetration testing and security assessment.
It covers topics such as the differences between black box and white box testing, the security assessment process, the different types of attacks, and the major stages of penetration testing and security assessment.
Installing and Configuring Kali Linux
This chapter provides detailed instructions on how to install and configure the Kali Linux operating system.
Related: Virtual Machines Step by Step (Kali Linux VM, Ubuntu, Windows)
It covers topics such as downloading and installing the operating system, setting up and customizing the environment, and configuring the system for specific testing scenarios.
Network Reconnaissance and Mapping
This chapter covers the process of network reconnaissance and mapping. It covers topics such as network discovery, port scanning, and service identification.
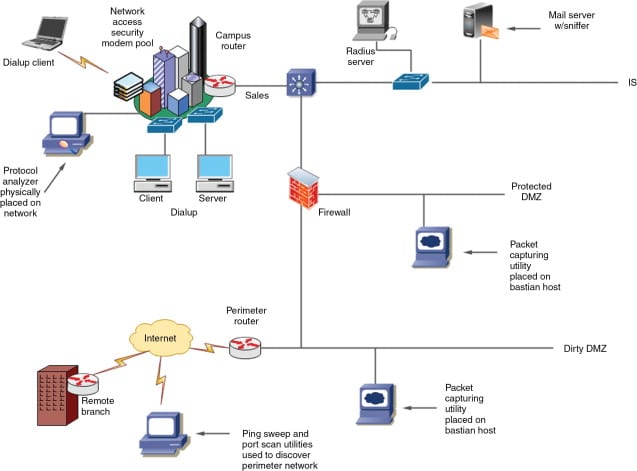
It also provides instructions on how to use the various tools included in Kali Linux to perform network reconnaissance and mapping.
Vulnerability Scanning
This chapter covers the process of vulnerability scanning. It covers topics such as identifying and exploiting vulnerabilities, using vulnerability scanners, and interpreting scan results.
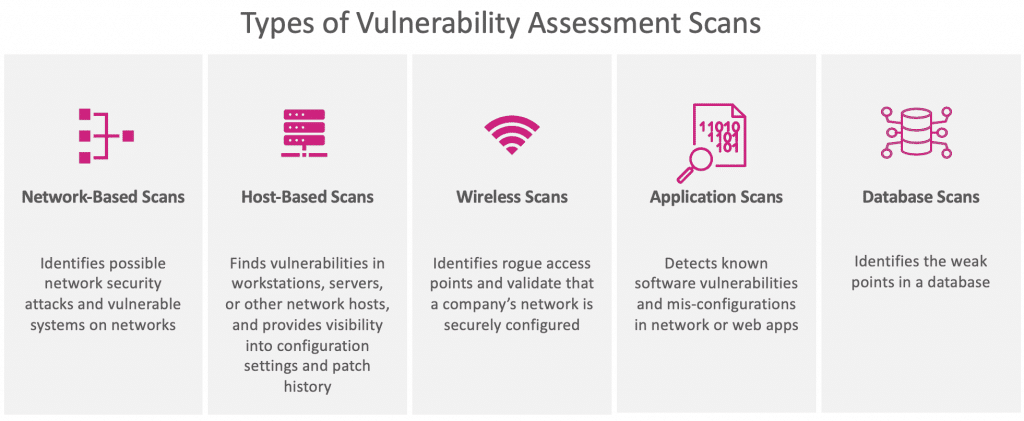
It also provides instructions on how to use the various tools included in Kali Linux to perform vulnerability scans.
Exploitation
This chapter covers the process of exploitation. It covers topics such as exploiting known vulnerabilities, writing exploit code, and bypassing security defenses.
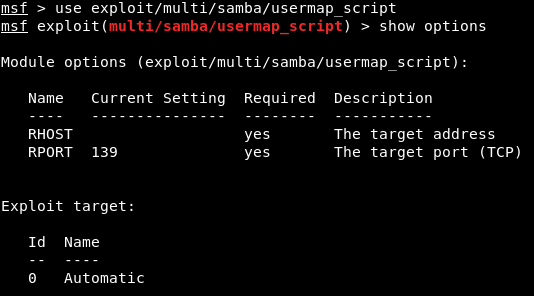
It also provides instructions on how to use the various tools included in Kali Linux to perform exploitation.
Privilege Escalation
This chapter covers the process of privilege escalation. It covers topics such as exploiting misconfigured systems, exploiting weak passwords, and exploiting system vulnerabilities.
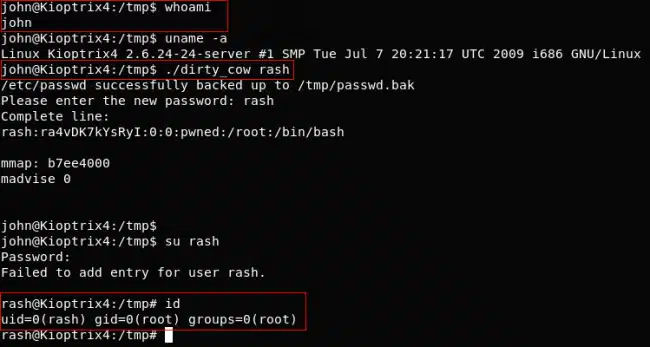
It also provides instructions on how to use the various tools included in Kali Linux to perform privilege escalation.
Password Cracking
This chapter covers the process of password cracking. It covers topics such as dictionary attacks, brute-force attacks, and rainbow table attacks.
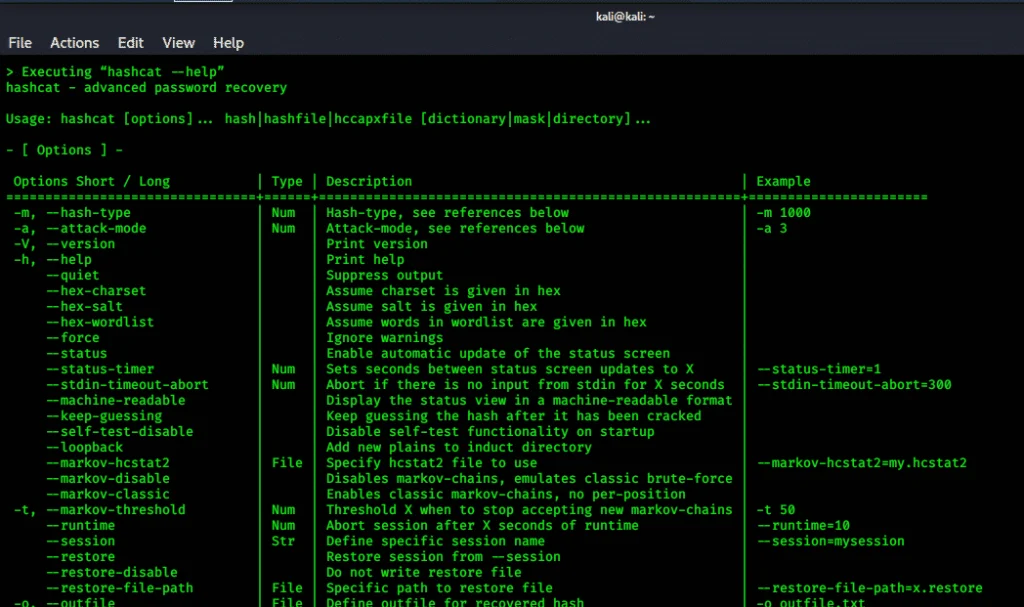
It also provides instructions on how to use the various tools included in Kali Linux to perform password cracking.
Post-Exploitation
This chapter covers the process of post-exploitation. It covers topics such as data exfiltration, pivoting, and maintaining access.
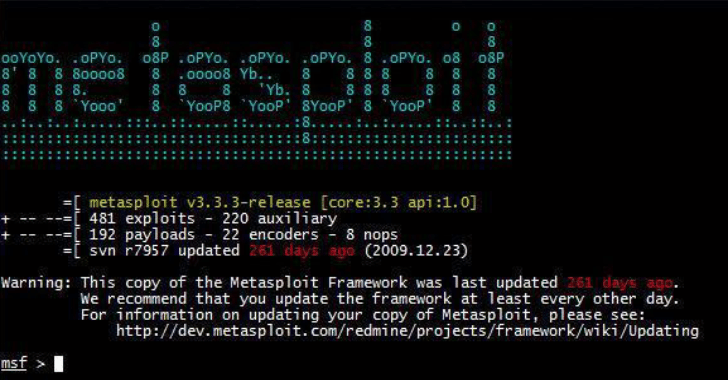
It also provides instructions on how to use the various tools included in Kali Linux to perform post-exploitation.
Reporting
This chapter covers the process of reporting. It covers topics such as creating comprehensive reports, documenting evidence, and presenting findings.
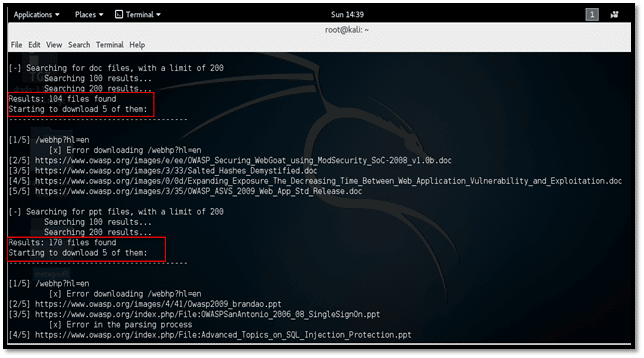
It also provides instructions on how to use the various tools included in Kali Linux to generate reports.
Attack Strategies and Defense
This chapter covers topics such as developing attack strategies, defending against attacks, and responding to incidents.

It also provides instructions on how to use the various tools included in Kali Linux to develop attack strategies and defend against them.
Tools and Customization
This chapter covers topics such as customizing the Kali Linux operating system, using Kali Linux tools, and deploying Kali Linux in the cloud. It also provides instructions on how to use the various tools included in Kali Linux to customize the system for specific testing scenarios.
Real-World Examples
This chapter provides real-world examples of penetration testing in action. It covers topics such as discovering and exploiting vulnerabilities, escalating privileges, and exfiltrating data. It also provides instructions on how to use the various tools included in Kali Linux to perform these tasks.
Download Kali Linux Penetration Testing Bible PDF Book Here
Here is where we share source of knowledge (Life Hacks & Life Style ), Entertainment, Technology, Fashion, E-News and updates all over the world.
Keep on visit our website for more updates
